LGE Mobile USB Serial Port (COM5) is a windows driver. It's released by Type: Version: 4.9.4.0 Date: 2008-11-11 Hardware IDs: USB VID1004&PID6000DIAGInterface Compatible IDs: The following operating system has used this driver: Microsoft Windows XP Professional Microsoft Windows 7 Ultimate Microsoft Windows XP Home Edition Microsoft Windows Vista Ultimate Microsoft Windows 7 Home Premium Microsoft Windows 7 Professional Microsoft Windows V This download is valid for the product(s) listed below: -Semp Toshiba Informatica Ltda - STI POSITIVO - POS-MI945AA ECS - 945GCT-M -N D - N/A Acer, inc. Aspire 4520 PCCHIPS - P17G PCCHIPS - A13G HCL Infosystems Limited - Notebook PC Positivo Informatica S/A - POS-MIG31AG To Be Filled By O.E.M. To Be Filled By O.E.M. HP-Pavilion - AY672AA-AC4 p6330br LI Computadores - Industria e Comercio Ltda. Syntax Notus VIA - K7VM3 ASUSTeK Computer INC. A7N8X2.0 OEM - 671 Acer - TravelMate 4050 MICRO-STAR INTERNATIONAL CO., LTD - Notices: The software drivers provided on this page are generic versions and can be used for general purposes.
However, computer original equipment manufacturers (OEMs) may have altered the features, incorporated customizations, or made other changes to the software or software packaging they provide. To avoid any potential installation incompatibilities on your OEM system, We recommend that you check with your OEM and use the software provided via your system manufacturer. We or the computer original equipment manufacturer (OEM) may not provide technical support for some or all issues that could arise from the usage of this generic version of software drivers.
Welcome to the forum. Please remove any usb or external drives from the computer before you run this scan! Please download and run to your desktop. Close out the program Don't Fix anything!
Don't run any other options, they're not all bad!!!!!!! Post back the report which should be located on your desktop. (please don't put logs in code or quotes) P2P Warning. Please read the directions carefully so you don't end up deleting something that is good!! If in doubt about an entry.please ask or choose Skip!!!!
Don't Delete anything unless instructed to! If you get the warning about a file UnsignedFile.Multi.Generic or LockedFile.Multi.Generic please choose Skip and click on Continue If a suspicious object is detected, the default action will be Skip, click on Continue Please note that TDSSKiller can be run in safe mode if needed. Here's a video that explains how to run it if needed.
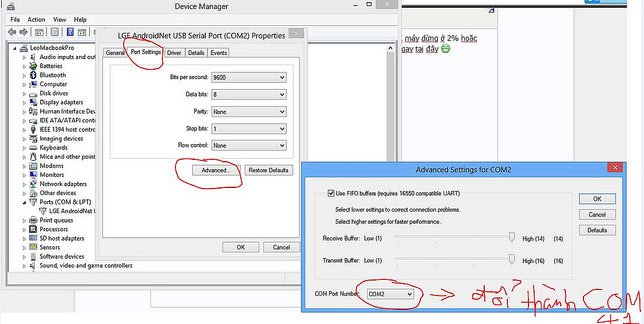
Lge Androidnet Usb Serial Port Drivers For Mac Windows 10
Please download the latest version of TDSSKiller from and save it to your Desktop. Doubleclick on TDSSKiller.exe to run the application, then click on Change parameters. Put a checkmark beside loaded modules.
A reboot will be needed to apply the changes. TDSSKiller will launch automatically after the reboot. Also your computer may seem very slow and unusable. This is normal. Give it enough time to load your background programs.
Then click on Change parameters in TDSSKiller. Check all boxes then click OK.
Click the Start Scan button. The scan should take no longer than 2 minutes. If a suspicious object is detected, the default action will be Skip, click on Continue. Any entries like this: Device Harddisk0 DR0 ( TDSS File System ) - please choose Skip. If in doubt about an entry.please ask or choose Skip. If malicious objects are found, they will show in the Scan results - Select action for found objects and offer three options.
Ensure Cure (default) is selected, then click Continue Reboot now to finish the cleaning process. Note: If Cure is not available, please choose Skip instead, do not choose Delete unless instructed.
A report will be created in your root directory, (usually C: folder) in the form of ' TDSSKiller.VersionDateTimelog.txt'. Please copy and paste the contents of that file here.
There may be 3 logs so post or attach all of them. Sometimes these logs can be very large, in that case please attach it or zip it up and attach it. Here's a summary of what to do if you would like to print it out: If in doubt about an entry.please ask or choose Skip Don't Delete anything unless instructed to! If a suspicious object is detected, the default action will be Skip, click on Continue If you get the warning about a file UnsignedFile.Multi.Generic or LockedFile.Multi.Generic please choose Skip and click on Continue Any entries like this: Device Harddisk0 DR0 ( TDSS File System ) - please choose Skip. If malicious objects are found, they will show in the Scan results and offer three (3) options. Ensure Cure is selected, then click Continue = Reboot now to finish the cleaning process.
Note: If Cure is not available, please choose Skip instead, do not choose Delete unless instructed. You can attach the logs if they're too long: Bottom right corner of this page. New window that comes up.
I forgot to mention after running Rogue Killer it automatically quarantined an item: PhysicalDrive0User.dat I posted the report from the RK scan in my last post, but what should I do with this quarantined item. Next I ran the Kapersky TDSSKiller scan. It found some suspicious items, but nothing it classified as malicious. I didn't see any option for Cure or anything like that. I haven't run anything else since we started this process, but why do you think it is that prior to this MalwareBytes and MalwareBytes Rootkit beta were still showing that a rootkit and other malicious items were found.
Do you think these are false positives? And what accounts for them to appear to be cleared and then reappear again later?
Anyway, the report from the TDSSK scan was too long to post, so I attached it. I found it again. It was called DocumentumCheckout, Export, Logs, Temp, UCF and Viewed. It also contains the files documentum.ini and documentum.lck. All of it was created April 26, 2013 @ 4:43:48 PM. The folders all appear to be empty though, except for the UCF folder which contains two xml files: ucf.installs.config.xml and ucf.launcher.config.xml and the Logs folder which has 2 ucf trace logs.
The UCF folder also has a sub-folder with my user name and within it a Shared folder which contains among many things a Jacob.jar and a jacob.dll and other.jar and.dll files. All this is related to the hack, right? Should I delete or do we need this in order to know what and how to fix?
Sorry, I am following your instruction, the other thing I just noticed in between while waiting for your reply. Yes, as I mentioned in my intial post I already ran several programs to try to get rid of it before I read the instructions on the forum. They all seemed to find the malware and offer to quarantine, clean or delete but as I mentioned it's very persistent and seemd to come right back.
And then of course I ran a bunch of things a year ago, when it was infected before, but that was too long ago to remember exactly. I think I ended up having to run ComboFix to get rid of it then and afterwords I started running Trend Micro RUBotted, but it didnt seem to help in avoiding this. This is a company machine and it has Symantec Anti-Virus Protection on it as the resident AV of their choosing. It runs regular periodic scans and I update the virus definitions fairly regularly.
Lg Serial Port Driver
I personally always start with MalwareBytes because I've had good success with that historically. To the best of my recollection, after that I tried some of the other TrendMicro products: RKill, rootkit buster and HiJackThis.
I can't seem to find any logs for those. Then I went the Kapersky route and tried TDSSKiller but it didn't find much.
Then after reading through the forum I learned about MBAR and tried that. That seemed to work great, but as I said, it seems to keep coming back.
Oh and I also ran AdwCleaner. I then ran a FRST scan in anticipation that would be required for assistance on the forum, but then when I went to post I saw the instruction for DDS logs instead. Since then you had me run RogueKiller and then TDSSKiller (again). Which leads us to the here & now. The logs I could find are attached.
I said I had a rootkit because that is what some of the programs that I mentioned reported to find. You should be able to see this in the logs I posted. Particularly if you look at the first scans. But as I mentioned if you look at the repeated scans of MBAR and MBAM one scan will find the Malware, the next will not, but then later it's back again. Sorry, if this is just a result of my ignorance, but I want to be sure the machine is clean. Even if clean it is still demonstrating many problems and generally not running well. So either the hacker or my attempts to get rid have resulted in damage.
I'm hoping there is a way to fix that or restore it back to it's previous condition. In particular, I really need my Outlook corporate email to function properly and I want to make sure I'm not going to spread any infections to someone else. SystemLook 30.07.11 by jpshortstuff Log created at 18:41 on by joel.hammond (Limited User) DIR c: documents and settings joel.hammond Documentum - Parameters: '(none)' -Files- documentum.ini -a- 94 bytes 20:43 20:43 documentum.lck -a- 0 bytes 20:43 20:43 -Folders- Checkout d- 20:43 Export d- 20:43 Logs d- 20:43 Temp d- 20:43 ucf d- 20:43 Viewed d- 20:43 -= EOF =- I'm not familiar with Kaseya, although I do know our company puts Monitoring SW on our machines which might have the same effect. Since I got hacked a year ago, I started noticing a program that lags on shutdown and has to be force closed by Windows. Update browser for mac.
I only see the popup briefly before it closes and shuts down, but the header bar is titled 'FullWindowsOwner.' Have you ever come across that one before? That folder seems to belongs to EMC Documentum Platform Essentials, sound familiar? Download, install, update and run a scan with SUPERAntiSpyware Portable Scanner: It's going to find a lot of cookies, so don't be alarmed.
Download aswMBR to your desktop. Double click the aswMBR.exe to run it. If you see this question: Would you like to download latest Avast! Virus definitions?' Click the 'Scan' button to start scan.
On completion of the scan click 'Save log', save it to your desktop and post in your next reply. AswMBR will create MBR.dat file on your desktop.
This is a copy of your MBR. Do NOT delete it.